In the era of embedded systems and custom solutions, ranging from interactive kiosks in public areas to the sophisticated control panels for industrial machinery, a crucial aspect of bespoke design is the ability to control and limit user interaction with the underlying system. The goal is twofold: to ensure a focused and secure user experience and to prevent unauthorized access or tampering. In this context, the keyboard filter emerges as a simple yet essential tool for achieving these objectives.
Why limit key combinations?
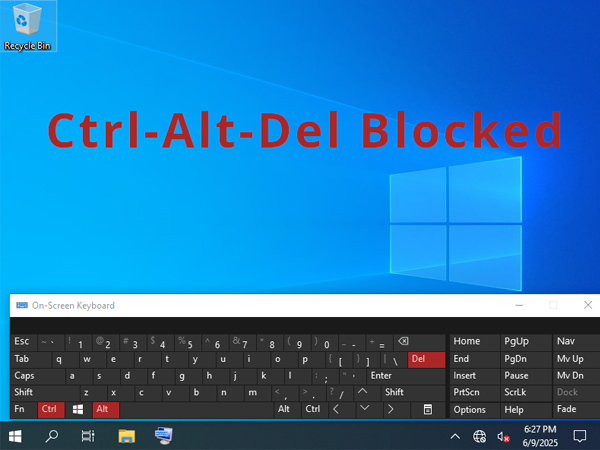
An operating system’s standard key combinations, such as Ctrl+Alt+Delete, Alt+Tab, or the Windows key, offer the general user the ability to access system functions, switch applications, open the Task Manager, or navigate between windows. While these are useful shortcuts in a traditional desktop environment, they become potential hazards in an embedded context.
Consider an informational kiosk in a public place: the user must only be able to interact with the application dedicated to providing information. You want to eliminate the possibility of them opening a web browser, accessing the control panel, or, even worse, attempting to shut down or restart the system in an uncontrolled manner. Similarly, in the field of industrial machinery, where operator panels manage delicate processes, it is essential to prevent unauthorized or simply clumsy operators from accessing critical configurations, executing irrelevant commands, or compromising the system’s stability through unintentional or deliberate key combinations.
The keyboard filter addresses this very need, allowing user interface designers to “lock down” the system by disabling or redirecting specific key combinations that would otherwise grant access to resources or features not intended for the general user.
Which key combinations are typically filtered?
The most frequently filtered key combinations include those that activate high-level system functions or allow users to escape from the full-screen application:
Ctrl+Alt+Delete: Often associated with accessing Windows security options (Task Manager, switch user, shut down).Alt+TabandAlt+Shift+Tab: Allow switching between open applications.Windows key: Opens the Start menu or, in combination with other keys (Win+Rfor Run,Win+Dto show the desktop, etc.), launches various system features.Alt+F4: Closes the active window.Ctrl+Shift+Esc: Opens the Task Manager directly.
By filtering these and other combinations, it is ensured that the user remains confined within the intended application, creating a controlled user experience and drastically reducing the chances of unwanted access.
Security and Tamper Prevention
Beyond shaping the user experience, the keyboard filter plays a crucial role in the security of custom systems. By preventing access to tools like the Task Manager, it becomes more difficult for a malicious user to terminate critical processes of the main application or launch unauthorized programs. In an industrial context, this translates to greater protection against unauthorized access to sensitive data or control functions that could compromise production or operator safety. The filter helps create a more robust and resilient operating environment, resistant to tampering attempts or human error.
Different Policies for Different Users
One of the great strengths of the keyboard filter, especially in systems with different access levels (such as operator panels on industrial machinery), is the ability to apply different policies depending on the logged-in user. By managing various user profiles, the system can be configured so that an administrator or users with elevated privileges have full access to all operating system features, maintaining the convenience of an “open” environment for maintenance and configuration tasks. At the same time, strict restrictions can be applied to standard operators or public kiosk users via the keyboard filter, limiting their interactions exclusively to the specific application for which the system was designed. This granularity in access control is fundamental for balancing security and usability in environments with diverse user types.
Conclusion
In summary, implementing an effective keyboard filter is an indispensable step in creating secure, stable, and user-focused custom operating systems. It allows for the precise definition of permitted interactions, the protection of critical resources, and the adaptation of restriction levels to the specific needs of different user profiles.
To discover how to best control your operating system and limit undesired access to certain areas of the system, contact us today through our contact page.